I can help you protect your desktop PCs with Enterprise-grade Huntress endpoint monitoring and event response agents running on Mac or Windows PC. Get a 24/7 managed security operations centre protecting your IT infrastructure. Access to my Readiness and Coaching interactive programme.
Long-term including local Tomachi Corp phone and email support for free open-source Linux software such as WordPress, and fast local immutable backups service in Avondale.
100K+
Secured Organizations
3M+
Managed Endpoints
5K+
Kick-ass Partners

Are you prepared for an IT dumpster fire and/or do you have your post-ransomware cyber-attack remediation plan in place? How about cyber-insurance? Let Tomachi Corporation tailor for you a customised cyber-security framework for your business, based on NIST CSF 2.0 (SP 1299), and based on your industry category, size and desired security posture. Get Cyber-Insurance Quote
The average cost of ransomware attack is $2,450/day* lasting 21 days…
 Tomachi Corporation just launched a fast local cloud backup service in Auckland to support Percussion Information Security New Zealand newest InfoSec service.
Tomachi Corporation just launched a fast local cloud backup service in Auckland to support Percussion Information Security New Zealand newest InfoSec service.
Businesses within 10 km are being contacted as part of initial market research project to discover interest in a) staff training sessions + exams b) level 1 IT Tech Support or c) purchasing a 4TB NAS file server appliance with integrated 24/7 monitored human-led Network Operations Centre constantly scanning their internal and external network traffic doing the usual deep packet inspection, intrusion detection, and assisting with optional isolation and remediation. The 4TB NAS file-server appliance would be sold for $4,800 NZD and come with 5 years of protection (or $200/month),
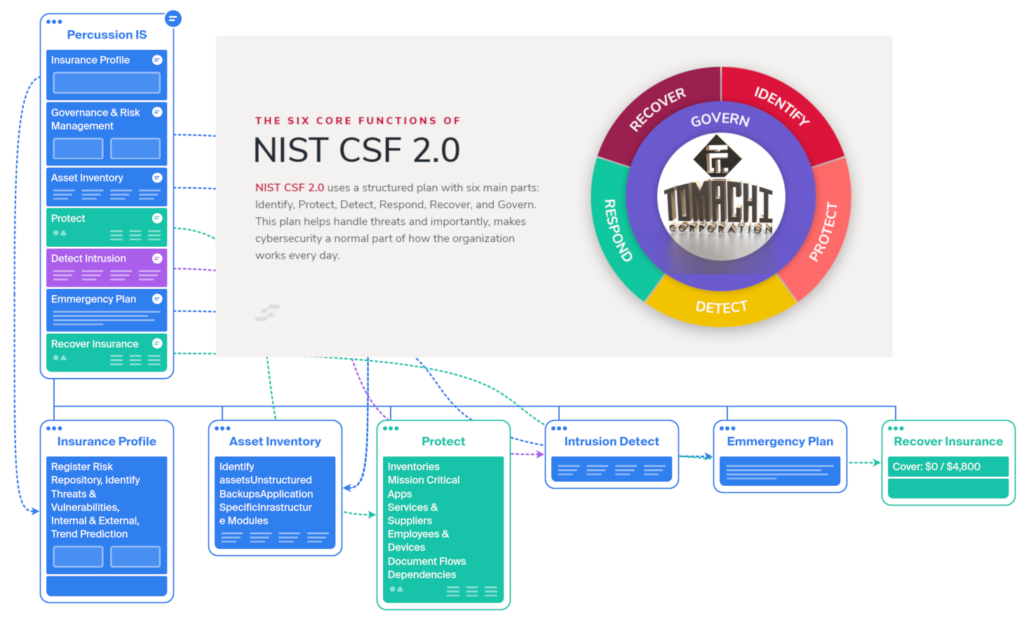
Develop and maintain a taxonomy of high-level cybersecurity outcomes to inform management of cybersecurity risk. Access community profiles and templates. Set Industry Category | Edit Organisational Profiles | Set CSF Tiers & Adjust Level of Cover | Progress Reporting/Rating | Deploy Plan Updates: Communicate Human Readable Versions | Export JSON | Upgrade Automation | Search Framework | Implement Compliance Modules: SMB, SCRM, ERM, FIPS, PCI, HIPA, ISO
Trying to gauge interest in short ~2-hour staff training events at New Lynn Community centre, aimed at medium sized employers to send their IT teams along to for professional development; where if attendees BYOD (bring their own device) during the first 30 to 45 minutes they can test their skill and help me to design version 1.0 of the InfosIQ test, similar to regular IQ test, get a score where “100 IQ” is a pass and ranks the person at the 50% percentile of population skill level distribution. Not NZQA approved but ultimately aiming to be, and based on NIST CSF.20 framework.
Are you interested in receiving certification on a basic 101 level covering the basics of social engineering attacks and ransomware operational security procedures? Customised for the relevant entity ID’s of attendees capacity of Meeting Room 1 is 20 to 35.
Tomachi Corp – based in Avondale – is an MSP specialising in Linux based open-source, but also including Office365 and a eventually a modular SaaS backup solution (coming 2025) for your cloud app data protection.
Ransomware attacks are not just momentary disruptions; they are prolonged battles. Recent data indicates that recovery from ransomware is about 21 days. This figure, however, doesn’t capture the life cycle and impact of the attack such as dwell time (the period from initial access to detonation) and business disruption, which could include significant loss of customer trust.
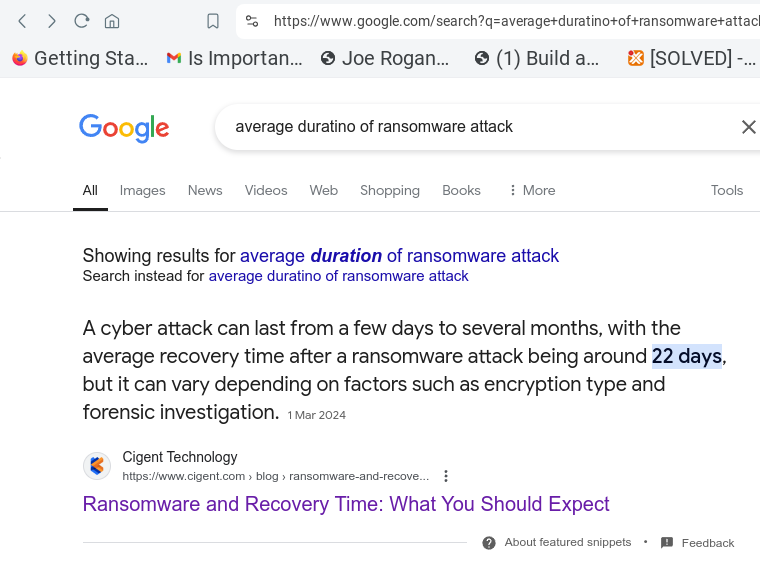
* 21 days from cigent.com/blog/ransomware-and-recovery-time-what-you-should-expect 22 days according to the Google snippet just now, 24 days statista.com/statistics/1275029/length-of-downtime-after-ransomware-attack-us/ 22 days Varonis varonis.com/blog/ransomware-statistics
Comparison to Bitdefender?
See: where we find that, in results validated by G2, actual users report:
- Huntress delivers nearly 2X faster ROI than Bitdefender GravityZone
- Huntress users deploy 2X faster than those using Bitdefender GravityZone
Schedule your free Huntress demo to experience the difference.