What you should be asking your penetration testing vendor?
We all know that pen-testing is a security best practice. As well as being required for compliance by some industries and clients.
Why consider pen-testing?
It would be so your can prove or disprove the real world plausibility of a successful attack.
Pentesting may be required as some contractual obligations as part of doing business with some customers.
Compliance is no guarantee of security, it should be a bare minimum best practice.
With the big headline attacks: Target, Sony, Mossack, Snowden et all, organisations now need to pay attention to real world threats. A pentest puts that human angle back into the mix.
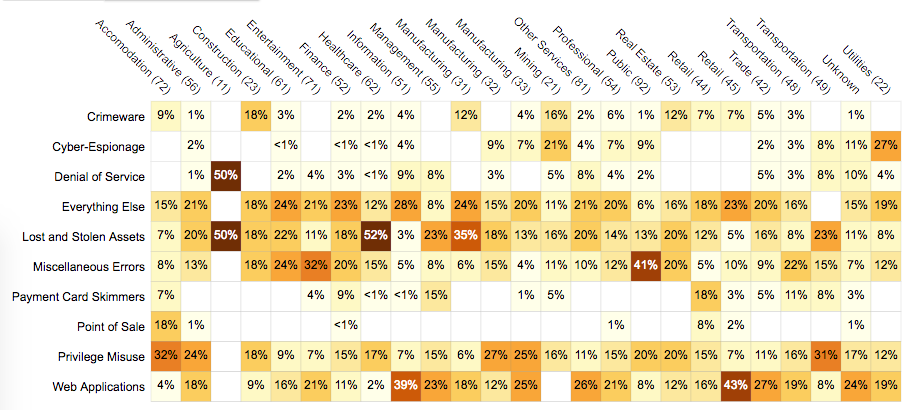
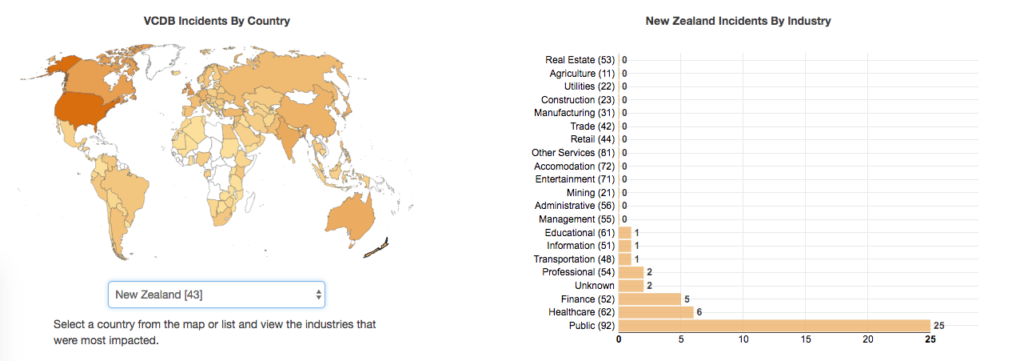
Chart of NZ info security incidents
It is also a golden opportunity to test out your incident detection and response quality is.
What is the difference between vulnerability scanning and pen testing?
A basic external vulnerability scan or “port scan” basically looks at your assets, and lists your known vulnerabilities where possible. But it doesn’t really validate those findings at all. A pentest goes further by proving or disproving the vuln and asking or answering the question:
What is the real world strength of your system against a determined human?
Note: it is important that you do not inform your IT security team ahead of the test in order to truly uncover issues.
How it’s done
 We start with a chat with the client. The initial scoping is very important. We look at the assets; third party systems; cloud based; 3rd party hosting. AWS allows you to request penetration testing notification, so their network ops can know it is taking place. Shodan; looking on Google. Port scanning; learn about infrastructure; which applications are used for access. network survey: open ports, services, authentication, un-authenticated services (printers), once we have a complete view of all the assets we are testing.
We start with a chat with the client. The initial scoping is very important. We look at the assets; third party systems; cloud based; 3rd party hosting. AWS allows you to request penetration testing notification, so their network ops can know it is taking place. Shodan; looking on Google. Port scanning; learn about infrastructure; which applications are used for access. network survey: open ports, services, authentication, un-authenticated services (printers), once we have a complete view of all the assets we are testing.
Low hanging fruit (wifi). First we start with automated tools, but also manually, with the information we already have, on the network side, and on the application side. if we find vulnerabilities, we may also develop exploits for these, depending on the amount of time is available. we then provide an actionable report for the client.
What penetration test execution standard will be used if any?
Ask for at least one free included “cycle” so you can re-test if your applied changes worked; prior to the final report.
methodology | validate findings | or take short cuts?
provides your organisation with a technical guide upon which tools are used in each part of the methodology.
Your application stack will be tested end-to-end. Inside-out. Outside-in. Inside-in.
What expertise do your experts have?
Are you able to provide a set of anonymised resumes, that can show your testers
active member of security community. have published papers that are recent.
Pentesting more than any other technical consultancy, is really down to the individual, or set of individuals.
Things to look for:
- certified ethical hackers
- holders of offensive security certifications
- published work
- industrial specialisation for example:
- medical org: embedded MRI, dialysis, pacemakers
- oil: Scada controls
- nuclear: siemens cyclotrons etc.
There is no replacement for experience.
You can’t take a grad, do a 6 week course, and expect to get the results you might get from say… Tomachi Corporation.
Considering how critical all of this is to your business…..
Look for pentesters with experience. Those that are active with software development. If you are going to test applicatoins, then you want someone who has experience delivering code. Someone with actual experience running enterprise infrastructure.
Data retention policy
Deletion policy should be published and executed. We’ll use the command line tool DOD standard 5220.22-M to securely erase your files after use.
Remediation Services
This one is a no brainer. You should be looking for a vendor that is able to help you remediate those uncovered risks.
Summary
- OWASP testing guide
- PCI Penetration testing guide
- Penetration Testing Execution Standard
- NIST 800-115
- Penetration Testing Framework
- Information Systems Security Assessment Framework (ISSAF)
- Open Source Security Testing Methodology Manual (“OSSTMM”)
Penetration Testing Execution Standard (PTES)
PTES defines penetration testing as 7 phases.
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting